OS Command Injection
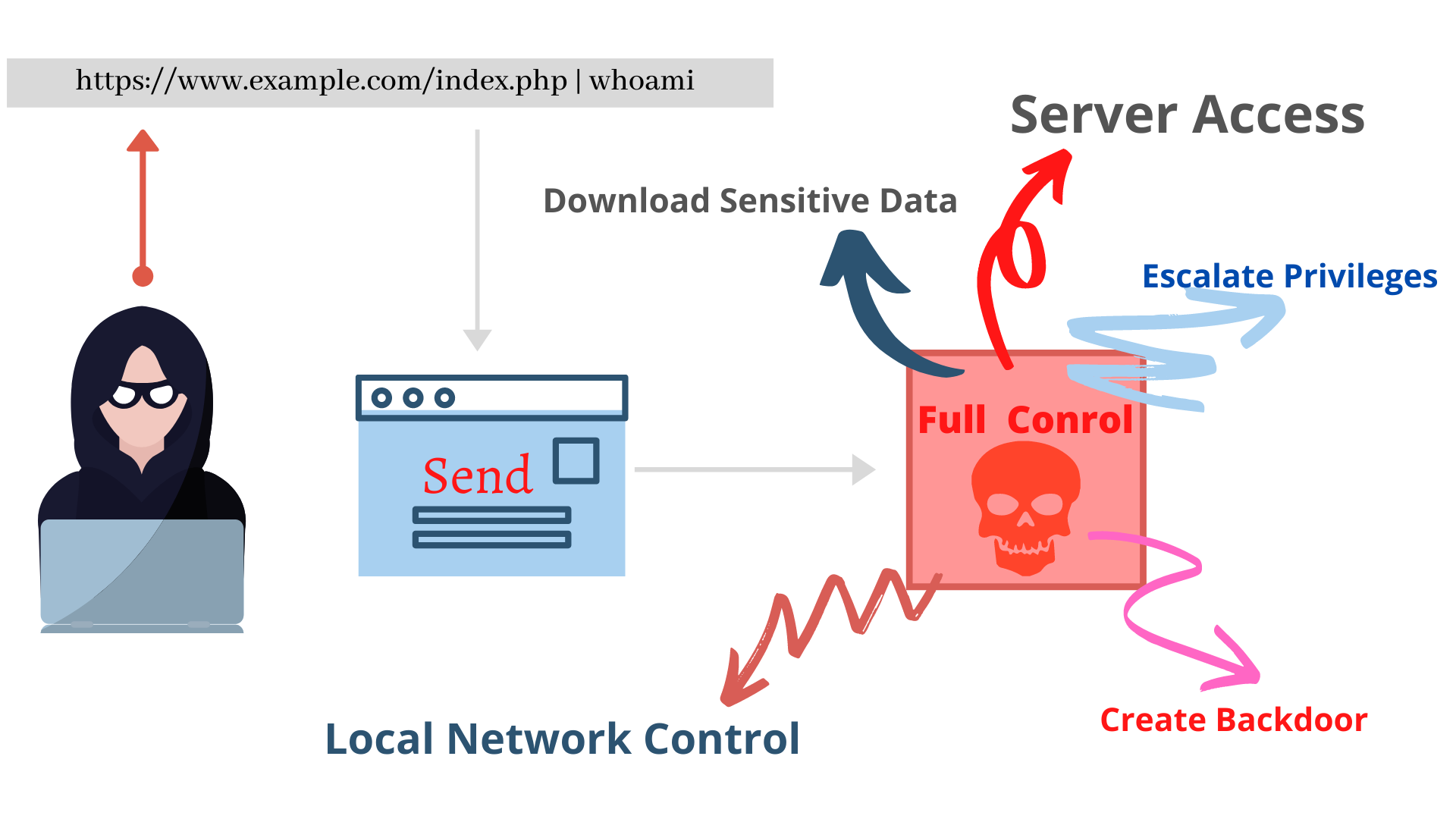

This is a web application vulnerability that allows an attacker to execute arbitrary operating system commands on the web server thereby compromising it completely. This typically occurs if there is no validation of the user-supplied input and the os commands are being being called directly from the web application, and being run on a system shell.
NOTE : The Commands passed in the query run with the privileges of the vulnerable application.
For example : Let us consider a C program that lets you view the files in the current directory.
#include
#include
int main(void)
{
DIR *d;
struct dirent *dir;
d = opendir(".");
if (d)
{
while ((dir = readdir(d)) != NULL)
{
printf("%s\n", dir->d_name);
}
closedir(d);
}
return(0);
}
Lets save this is dirlist and check the output.
$ ./dirlist
OUTPUT : temp.c 1.c 2.c
If I add a semicolon and add another command to it, then becomes a classic example of Command Injection, where we are just extending the default functionality of the program.
$ ./dirlist ; cat 1.c
OUTPUT : temp.c 1.c 2.c
#include
int main()
{
printf("This is for testing purposes only");
return 0;
}
You may note that both the program and our command ran successfully.
As I had mentioned earlier that the command runs with the privileges of the application. However, if the permission given to the application are that of the root user (Administrator in windows) this can be disasterous.
Lets consider a website that uses a script to check the commodities.
https://www.example.com/Cycles?ID=123&countryID=123
Suppose, in the server, a script called ape.py is run with ID and countryID as its parameters.
ape.py 123 123
It returns an output of 11210.This is then fetched and displayed on the website.
However if the user tampers with the query, he can cause the server to run arbitiary commands.
Let us suppose he Injects the following command & echo `whoami` & in the url.
The resulting URL becomes:
https://www.example.com/Cycles?ID=123 & echo `whoami` & &countryID=123
This is run on the server end as,
ape.py 123 & echo `whoami` & 123
This results in :
11210
www-data
You may note that not only did it return the data, but the name of the user, with whose privileges commands are being run.
Some other useful commands that you could use :
| Process | Linux | Windows |
|---|---|---|
| Operating System | uname -a | ver |
| Network Config | ifconfig | ifconfig /all |
| File Contents | cat filename | cat filename |
| List Files | ls | ls |
| Running Processes | ps -ef | takslist |
One of the ways of preventing Command injection is by sanitizing the input and perforing validation on it.
The second way could be to never call out OS commands from the application.
The best Ways to validate are:
Sometimes, it is also possible that a web application is vulnerable to OS Command Injection but doesn't just throw the information out.
For instance, while submitting a feedback form, the attacker injects & `whoami` & into the contents.But after the submission of the form there is nothing that the server has to return so the attacker can't validate whether the application is vulnerable.
Fortunately there are other ways to check for Blink OS Command Injection. Learn about it here
I've been showing you commands beginning and terminating with |.
This is equivalent to OR in linux and windows.
You can try different command seperators. Below is the list of separators that you could try.
The following only works on unix-based systems.