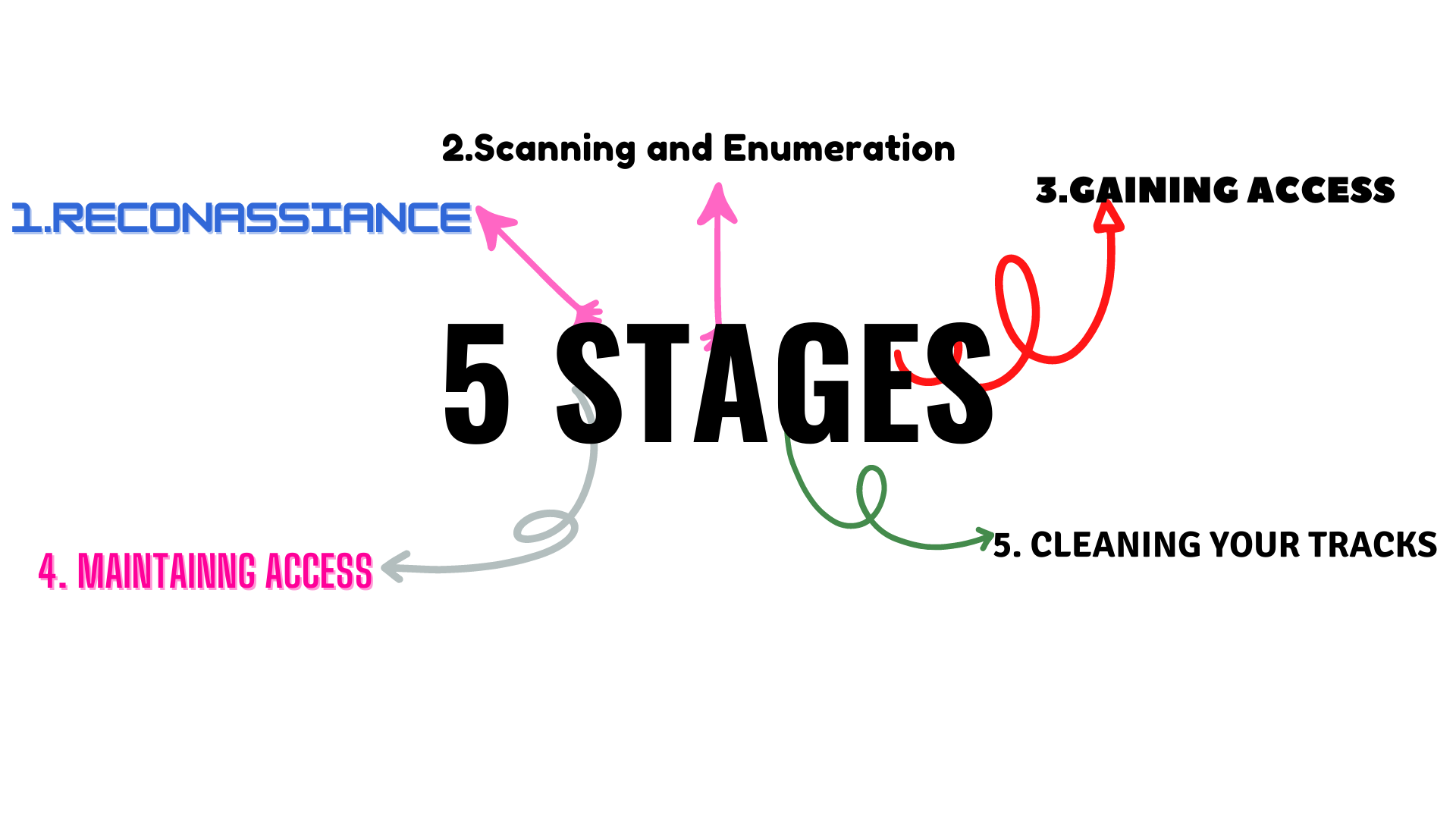
A good ethical hacker makes sure that he's left no stone unturned
be it during a pentest, while playing CTFs and the list goes on.
The entire process, from getting a machine to exploiting it, has been divided into 5 stages.